Android
Big security issue: You can easily break security of any Samsung Galaxy device
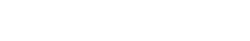
Samsung always keeps security as a priority when it comes to Galaxy devices. Meanwhile, there are still some issues from the Android side, which are still compromising security. In a recent development, our team member found a YouTube video, showing that you can destroy any Samsung device’s security in just a minute, is it an issue?
A YouTube channel posted plenty of videos guiding users on how they can factory reset their Galaxy device in case of forgetting the password, pin, or pattern. Since a manual reset stops you to use your device without logging in with the same Google account the phone had before, the YouTuber even bypassed FRP.
Follow Sammy Fans on Google News
The video begins with a short introduction on breaking any form of security lock on all Galaxy devices. Seeing this video, we followed the same steps and found that the method is accurately working and we were able to factory reset Galaxy devices, including:
- Galaxy Z Fold 4
- Galaxy Z Flip 4
- Galaxy S22 Ultra
- Galaxy Z Fold 3
- Galaxy S21 and S21 FE
- Galaxy M31 and A30s
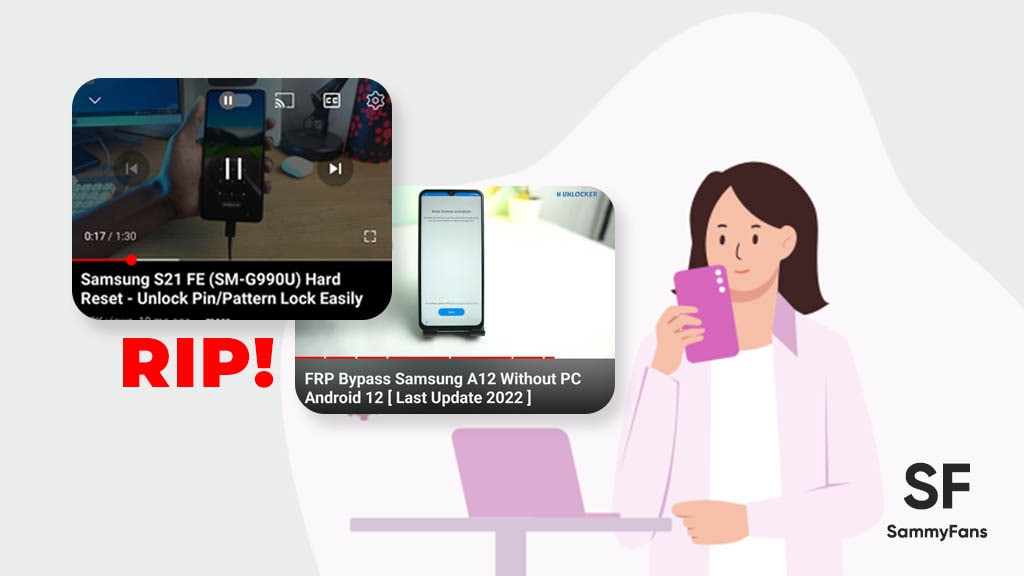
As shown in the video, you can break any Galaxy device’s lock (password, PIN or pattern) by resetting manually. To do so, just plug in the USB and connect it to a PC, and press all three physical buttons simultaneously. As soon as your device turns off, leave the volume down button, followed by the power button a few seconds later.
Join Sammy Fans on Telegram
Within seconds, you will be able to access the recovery mode of Android, letting you install the firmware manually, and wipe system data as well as cache. Using the Wipe data/factory reset option, you can hard reset any Galaxy device, while the FRP can also be bypassed with a handful of head-scratching steps.
I shocked seeing Samsung Knox also validated installation of a third-party root access apps!
While this method would not leave any kind of personal data or account logged in in the Galaxy device, but, you won’t be able to trace it through services like Find My Mobile. In case of misplacement or theft incidents, anyone can get access to use your Galaxy device as a first-hand user.
Users’ personal data won’t be accessible by gaining access to factory reset and FRP bypass methods. Still, we are disappointed to see that the user eventually used Samsung’s setup wizard as concluding the method of getting complete access to the Galaxy device.
Samsung should look into the matter and fix the issue/bugs that provide unauthorized access, destroying security promises. The company should also work with Google to make the FRP and factory reset more reliable as some are still compromising users’ privacy.

Android
One UI 7 to bring Android 15’s secret Landroid screensaver

Android 15’s Easter Egg includes a secret Landroid screensaver mode that One UI 7 might borrow. Samsung’s next One UI iteration will be based on Android 15 OS. Core Android features such as Easter Egg will be included in Galaxy’s next major upgrade.
Debuted as a Landroid screensaver, Android 15’s Easter egg was added with the latest Beta. Google News Telegram channel’s Nail Sadykov discovered that the Easter egg game is equipped with an integrated screensaver mode.
To activate Easter Egg, head into Settings followed by About phone and Android version. Once done, tap the displayed Android version several times until you see the Android 15 bugdroid logo floating in space.
Space travel mini-game will be available to play added with Android 14. When you initially trigger the mini-game, you should have unlocked the new screensaver, tucked away under Settings → Display & Touch → Screen saver → Landroid.
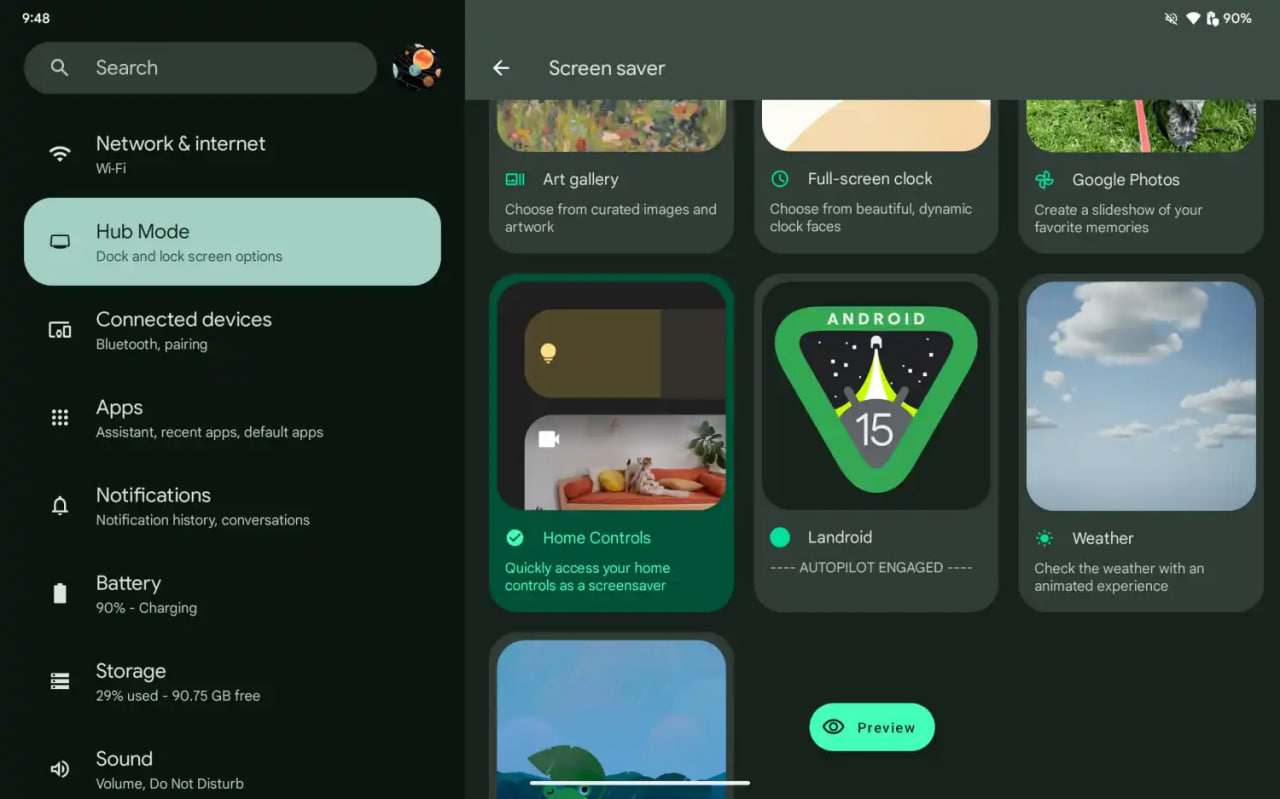
After activating the screensaver, you can set your phone on your desk. Now, the phone will let you watch the Easter egg game take over in autopilot mode, as the spacecraft automatically dodges planets – it provides a better experience on a tablet placed on a dock.
AI
Android 15 might let you share AI-generated wallpapers

Google introduced the AI Wallpaper feature with the Pixel 8 series. The same functionality is also available in Samsung’s Galaxy S24 series thanks to Genini Nano. Now, Google is preparing to make AI-generated wallpapers sharable with Android 15.
Pixel’s ability to create AI-generated wallpapers is quite popular among users. Currently, the feature only allows users to generate stunning wallpapers and apply on the home screen and lock screen. Sharing with someone presently requires to be saved as a screenshot.
Threads user @the_husbandalorian discovered interesting evidence in the latest Beta. The company is working on a new option in Android 15 to share AI-generated wallpapers. A new share button is added on the preview screen in the wallpaper picker interface.
Post by @the_husbandalorianView on Threads
The preview will display how the wallpaper will be applied to your phone’s home or lock screen. The pencil button will allow you to refine the prompt used to create the wallpaper. Share button is all you need to share AI-generated wallpaper with others.
At present, the ability to share AI-generated wallpaper is broken. It suggests the feature is still under development and requires additional work. The next Beta might make it functional for Beta users, and we guess public availability with a Stable rollout.
AI Wallpaper in One UI 6.1
Android
Samsung Android 15 Update: One UI 7 Ineligible Devices [LIST]

Samsung is very well known for its excellent after-sales service and software support. The company announced that it will provide up to 7 years of major OS upgrades and security updates for its flagship devices, starting with the Galaxy S24 series. This is a remarkable achievement that will allow Samsung users to enjoy the latest features and security enhancements for a long time.
Not all Samsung devices will be eligible for the upcoming Android 15-based One UI 7 update, which is expected to bring several new features and improvements. Some older and lower-end models of the Galaxy A, Galaxy M, and Galaxy F series have reached the end of their software upgrade cycles, and will not receive any further OS updates.
Follow our socials → Google News, Telegram, X (formerly Twitter), Facebook
However, these devices will still receive security patches for another year, but they will miss out on the new features and benefits of One UI 7.

Android 15 Easter Egg [Customized by Camila Foster, Sammy Fans]
Samsung Android 15 One UI 7 Ineligible Device List
The following is the list of Samsung devices that will not get the Android 15 One UI 7 update:
Galaxy A series
- Galaxy A04s
- Galaxy A13
- Galaxy A23
- Galaxy A72
- Galaxy A52
- Galaxy A52 5G
- Galaxy A52s
Galaxy M series
- Galaxy M53 5G
- Galaxy M33 5G
- Galaxy M23
Galaxy F series
- Galaxy F23
If you own any of these devices, you may want to consider upgrading to a newer model that will support One UI 7 and beyond.
Note: The list is compiled on software update policy and previous rollouts.